Content Security
Overview
The Content Security module is available from the Administration menu which is available to users with Administrator and Agency access rights. The module allows you to decide who, inside and outside your organisation, can view Structures and Data.
The module is simple and straight forward to use however before you embark on any implementation it is recommended that you spend some time planning out what you want to achieve before you start.
Principles of Operation
Depending on the setting specified in the Administration area, Security Settings, General, all structures are public by default. This means that you do not need to give specific access to any structures or data if you are using the Content Security module. The Security Module is to prevent access to the many by giving access to the few.
Key Concepts
- Content Security provides control over who can view structural metadata and observational data content.
- It does not control who can create and maintain structural metadata – this is managed by granting users membership of SDMX Agency organisations.
- It does not control who can submit, amend, or revise data – this is managed by granting users membership of SDMX Data Provider organisations.
- All structures and data are visible to all users unless Content Security rules are applied.
- The Server Security setting controls whether anonymous users are allowed in addition to authenticated users: Public – anonymous users are allowed, Private – only authenticated users.
- A Structure Rule restricts the visibility of a structure to members of specific Security Groups.
- Rules placed on a structure are inherited by any structures or data sets than depend on it.
- A Data Rule restricts the visibility of selected series or observations in a data set to members of a specific Security Groups.
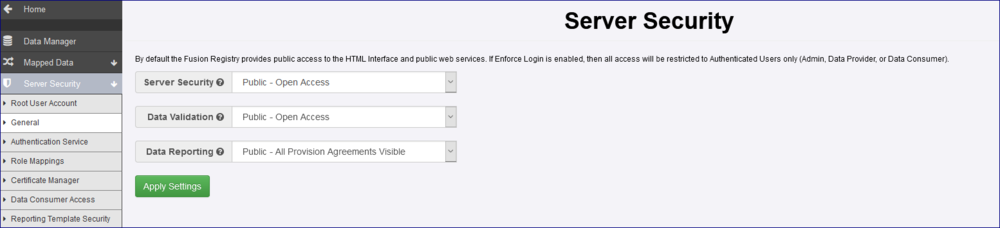
Server Security Setting
Below is an example of the Security Settings for a Registry which is fully ‘public’.