Difference between revisions of "Content Security - Active Directory"
Jump to navigation
Jump to search
(Created page with "Category:How_To If your organisation uses Active Directory and decides to implement Content Security, you may need to review your current Active Directory set up to ensure...") |
|||
| Line 1: | Line 1: | ||
[[Category:How_To]] | [[Category:How_To]] | ||
| + | [[Category:RegistrySecurity]] | ||
If your organisation uses Active Directory and decides to implement Content Security, you may need to review your current Active Directory set up to ensure you can achieve what you are aiming for by implementing Content Security. | If your organisation uses Active Directory and decides to implement Content Security, you may need to review your current Active Directory set up to ensure you can achieve what you are aiming for by implementing Content Security. | ||
Revision as of 05:03, 16 August 2023
If your organisation uses Active Directory and decides to implement Content Security, you may need to review your current Active Directory set up to ensure you can achieve what you are aiming for by implementing Content Security.
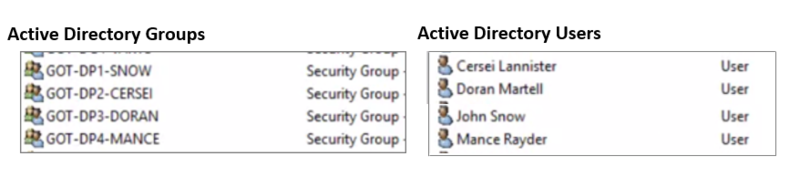
In the example used in this article which explains how to Set up Role Mappings, if you subsequently decided to use Content Security to change what each of the Data Providers could view using Content Security, you will need to put each AD user into their own unique AD Group as shown in the example below.